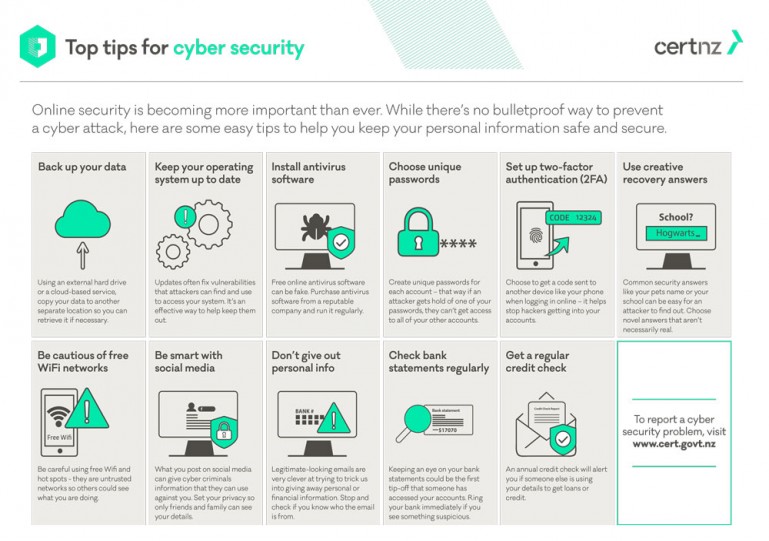
6 Easy Facts About Home Alarm Systems San Diego Shown
So it shows up that home safety and security systems assistance protect against residence thefts. The inquiry that remains which we concentrate on right here is laying out your house protection system options. Right here they are arranged by primary kinds. Safety and security systems can be found in different types and also functions, as well as selecting the most effective one for your residence can be exhausting if you just recognize a thing or 2 regarding them (home security systems san diego).
That being said, do comprehensive study to find the best safety system for your requirements. A monitored system alarm system is one of the most prominent security systems for home available in the market.
Commercial Alarm Systems San Diego - The Facts
This system comes in two kinds, the company-monitored security system and also self-monitored security systems. As the name suggests, self-monitored safety systems are those that you can keep track of and control on your own. These systems consist of activity sensing units, door sensors, safety video cameras, in addition to sirens that call or text your cellphone when triggered.
Additionally, this system additionally gives you the option of either calling 911 or asking a neighbor to inspect for indicators of a break-in whenever you receive a notice and you're not in your home. Although self-monitored safety and security systems are thought about contemporary and also effective, they still have their fair share of benefits and drawbacks - home security companies san diego.
They are convenient and also can be quickly transferred to one more area or new house because you can mount and also uninstall the systems on your own. Their camera systems can keep an eye on as well as videotape video evidence of trespassers. Self-monitored safety and security systems are cost effective. Self-monitored safety and security systems require a Wifi connection to work. It will certainly not operate in case there's a power outage.
Commercial Alarm Systems San Diego Things To Know Before You Buy

Even though every system has various features, the majority of company-monitored safety systems are constructed to caution their particular get in touch with facilities whenever an invader breaks in at your house while the system is equipped. Moreover, you will certainly additionally obtain a confirmation call to check if the alarm was not triggered by error.
Some systems are also suitable with smart devices which allows you to check the screen from another location. They offer a good level of security even though it's not as sophisticated as well as comprehensive like monitored systems. These systems commonly give self-run or more static safety systems which make them easier to make use of and also operate.
Getting The Home Security Systems San Diego To Work
The majority of unmonitored security systems are heavily reliant on the owner. Unmonitored security systems are much less safe as well as durable than monitored safety systems.
Easy to mount and uninstall. It will be very easy to take your house alarm with you in case you intend to transform its location or you will relocate to another home. These systems additional hints are offered in DIY packages. You can install and also make them up as well as running no time at all as there's no requirement to pierce openings and also complex wiring to establish.
Since the systems aren't hard-wired, it's easy to update as well as transform them. A wireless house protection system is difficult for a burglar to disable due to the fact that there are no cords affixed between the control panel and discovery tool.
4 Simple Techniques For Home Security Systems San Diego
You will certainly need whole lots of batteries. Wireless detection devices generally need batteries to function. Thus, the batteries require to be changed as needed and also sensors will certainly need to be periodically checked. If you have a big residence, you will require more to check-in. Prone to hacking. It will certainly be feasible for an intruder to block the signals as well as hack a cordless system.

All access factors of your residence will be wired back to the primary control board along with motion detectors, keypads, and website link various other safety gadgets. These hard-wired security system provide an extra reliable link than cordless systems since the primary panel knows the real-time status of each device within the system.
3 Simple Techniques For Home Security System San Diego
Intruders can merely cut the wirings and phone lines outside the residence should they desire to disable the protection system. A wired safety system equipment is hard to uninstall.
These sensing units are generally made use of to secure spaces with important products and also less-frequented locations in larger homes. These sensors are composed of 2 parts that adjoin each various other when mounted. A part of the device is positioned on the home window or door while the various other gets on the window sill or door frame.